Internet is great – you can browse all kinds of websites, engage with people around the globe on social media, shop online, stay entertained, and do a ton of other fun and useful things which would not have been possible had the WWW (World Wide Web) not been around.
However, is it safe to provide your personal and financial information online? There is no way you can get into a serious internet transaction, social or financial, without providing this information. But what if someone were to intercept the communication between your browser and the webserver to steal the information being exchanged (this is called MITM, or a man in the middle attack)? Now, that can be scary. Imagine someone getting access to your details and you becoming a victim of identity theft or someone emptying your bank account because they got hold of the information from a financial transaction you conducted online.
As a website owner, you must take care of these user concerns to sustain and grow your online business.
Is there a way to prevent data theft during data transactions? Of course, the SSL is the solution.
What is SSL?
SSL (Secure Sockets Layer) turns your plain HTTP text (where the data is transmitted in plain text) into HTTPS (HyperText Transfer Protocol Secure). HTTPS works by encrypting the data before it is put on the communication channel, and the other side decrypts it. The entire encryption process works in a manner where only the endpoints know how to encrypt and decrypt the exchanged data. So, even if a hacker launched a MITM attack on you, they will not be able to succeed in their malicious intent as they will not be able to make sense of the encrypted material.
How does SSL work?
SSL works by encryption, which can either be asymmetric or symmetric. Let us look at what these encryption mechanisms mean.
Asymmetric encryption
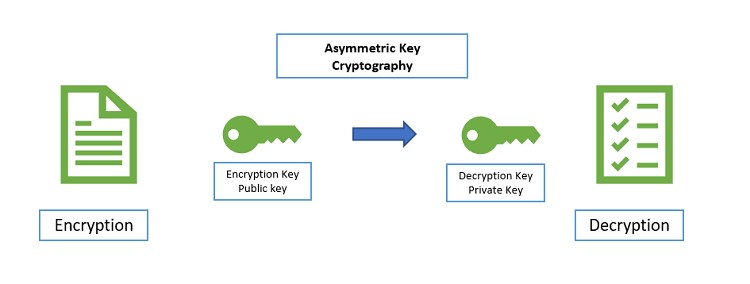
Also called Asymmetric cryptography, or public-key cryptography, this mechanism uses a mathematically generated pair of keys for encryption and decryption. The public key is shared with the party you want to communicate with, while you keep the private key as a well-protected secret that no one knows except you.
During data communication, the information is encoded using the private key and can only be decrypted by using the associated public key.
Symmetric encryption
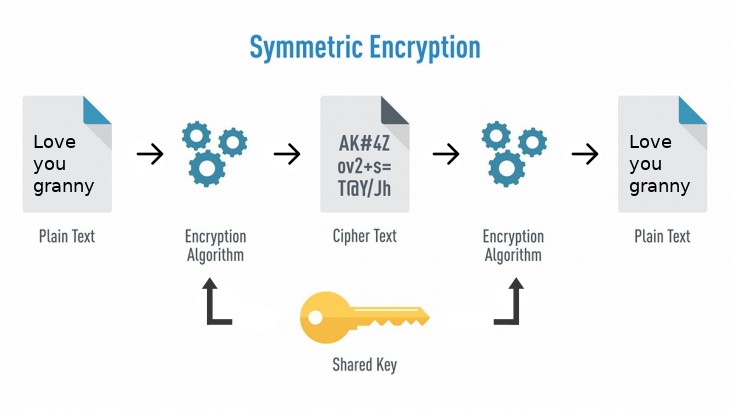
In Symmetric cryptography, there is no need for a private/public key pair – the same key is used at both ends for encryption and decryption.
There are two parts to SSL communication:
- Initial SSL handshake
- Actual SSL data transfer
SSL uses Asymmetric (Example algorithms: DSA, ElGamal, RSA, PKCS, and Elliptic curve techniques) cryptography in the initial handshake and Symmetric (Using algorithms such as AES-128, AES-192, and AES-256) encryption for the actual data transfer between the communication parties.
Let us now get deeper into the actual SSL communication process.
Initial SSL handshake
SSL communication always begins with an initial SSL handshake. This asymmetric communication where the browser verifies the authenticity of the webserver gets hold of the server’s public key and establishes the HTTPS connection for the actual data transfer.
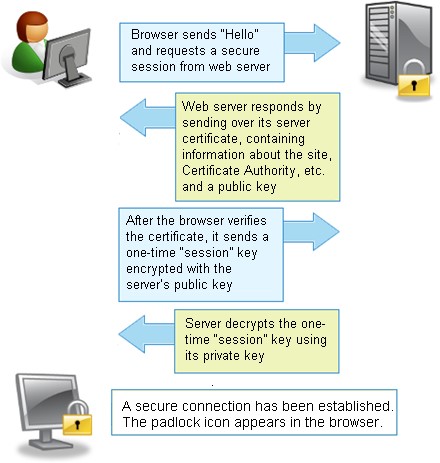
Here are the steps in of an SSL handshake:
- The client begins by sending a “client hello” to the server. This message includes information about the client, such as encryption settings, SSL version, session-specific data, etc. needed by the server to start communicating with the client over SSL.
- Once the server receives the “client hello,” it responds with a “server hello” message. This message includes server information such as encryption settings, SSL version, session-specific data, and its SSL certificate (which includes its public key), etc. that is needed by the client to begin using SSL to communicate with the server
- Before initiating any further communication, the client verifies the SSL certificate presented by the server with the CA (Certificate Authority). If the server authentication fails, the client shows a warning to the user and refuses the SSL connection.
- If the server is authenticated, the client encrypts (using the server’s public key) a session key it creates and sends it back to the server.
- On receiving the session key, the server uses its private key to decrypt the session key and sends back an encrypted (using the session key) acknowledgment to the client.
So, once the initial SSL handshake is complete, both the parties end up with a session key to be used for encryption and decryption of the exchanged data. The private and public SSL keys are not used any further in the communication.
Actual SSL data transfer
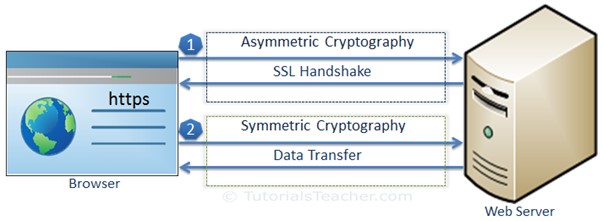
The actual data transfer between the client and the server uses symmetric cryptography with the shared session key used at both ends for encryption and decryption. The reason to use symmetric cryptography in the actual SSL data transfer is that symmetric encryption/decryption is less CPU intensive compared to Asymmetric cryptography.
Role of SSL certificates
Now that you understand how SSL works let us turn our attention to the role of SSL certificates. SSL certificates, also called digital certificates, are critical in establishing the secure HTTPS communication between the web server and client browser and If You want an ssl certificate to secure your website then You can get your certificate from ClickSSL, a reliable SSL provider that stocks a dynamic range of SSL certificates from some of the world’s best certificate authorities (CAs) at surprisingly low prices.
SSL certificate has been issued by a trusted CA (Certificate Authority). The SSL certificate carries the public key and other information about the certificate owner. During the SSL handshake process, the server sends its public key to the client by sharing its SSL certificate, which the client uses to authenticate the webserver with the CA.
The user can see the details of the SSL certificate on their browser too (every browser has a different way of presenting it, but the information is the same – verified and included in the SSL certificate by the CA)

There are many kinds of SSL certificates for you to pick from. The choice depends on the level of validation (yes, the CA will validate the identity of the entity requesting the SSL certificate using various levels of verification) you are prepared for and the number of domains/subdomains you want to protect.
Advantages of having an SSL certificate
Sounds good, right? Wait till you hear more.
Not only do you secure the information exchange between client and yourself, but there are also other perks of having an SSL certificate installed on your server.
Your users will see an indication on their web browsers (usually a green padlock on the address bar) to indicate that the communication is secured using SSL. This assures them that they can share personal and financial information with you without worrying about data theft during communication. Having this confidence means that they are more likely to engage with you at a deeper level and have a higher chance of conversion, which means more money in your pocket.
Not only that, but you also get targeted organic traffic from search engines when you use SSL. Yes, that is true. Search engines rank you higher on SEO (Search Engine Optimization) if your web pages use HTTPS. So, not having SSL is like leaving money on the table. Why would you not want more SEO traffic from the search engines, when it is proven beyond doubt that these visitors have a higher chance of converting as they are looking for what you have to offer?
How to get an SSL certificate?
Now that you understand the basics of SSL let us look at how you can get one. The certificate authorities like GeoTrust, Comodo, Symantec, etc. issue SSL certificates.All these certificate authorities including GeoTrust are the leading Certificate Authorities that you can request your SSL certificate from, and they offer the type of certificates to meet your needs.
When you decide to secure the website, you need to purchase SSL certificate let’s say if you buy GeoTrust SSL Certificate, you will need to share your domain name(s), physical address, business details, and other information that the CA will need to verify your identity. You may be asked for additional documents to support your claim over the domain and to establish your identity. The CA may take other steps like phone and domain verification to authenticate your request. The level of confirmation depends on the kind of SSL certificate you are seeking.
Once the CA is convinced of your identity and has verified your request, you will get your SSL certificate, which out can install on your web server and start reaping the benefits of having your site running on HTTPS.
In summary, hopefully, this article has delivered its promise. You must now have a good understanding of how SSL and SSL certificates work. Not only that, but you can also now better appreciate the benefits of having HTTPS on your website. Also, you have gained information of where to get your SSL certificate from. So, go ahead – Buy GeoTrust SSL Certificate and get on with your online success.
